Straight Talk About Disinformation and Ballot Fraud
John Sebes
Editor Note: We’ve combined two comments by our CTO John Sebes this week into a single article here because in this case they are tightly related to the lingering brouhaha over a recent attempt of voter intimidation initially attributed to a U.S. and Canadian far-right organization, the Proud Boys. John’s first comment (Part 1) is about the challenges of disinformation and attribution. His second comment (Part 2) is more specifically focused on the means of the intimidation stunt: overseas ballot fraud.
Part 1: Disambiguating Disinformation
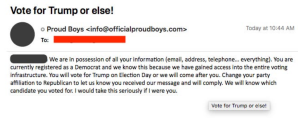
We had lots of conversations last week with media about disinformation vs. misinformation and in particular, a recent situation we monitored and helped other journalists assess. At first look it appeared to be a voter intimidation maneuver, but at closer look proved to be more of a hoax video designed simply to scare voters and essentially amounted to a voter suppression effort.
In light of the flurry of activity and stories such as this NY Times article, I’ll share here what I’ve been explaining to the media, starting with an answer to the basic question:
Is this legitimate or just more (Russian) disinformation?
One answer: You can’t tell. Therefore, it’s responsible to do three things:
- Start with the assumption that it is likely disinformation; but
- Do not amplify the message; and
- Assess newsworthiness based on its significance as possible disinformation.
 Yes, this is part of the “new normal:” nation state adversaries use disinformation to influence U.S. elections.
Yes, this is part of the “new normal:” nation state adversaries use disinformation to influence U.S. elections.
You would be misguided to look at the possible disinformation artifact (e.g., the social posting, eMail, video, etc.) and draw the conclusion that it is part of a disinformation attack. The artifact itself cannot tell you.
Attribution is difficult
You would also be mistaken to believe that by examining the artifact alone anyone could tell that it is attributed to a particular disinformation actor, nation state or otherwise. Attribution research can be complex (think: “3-dimensional contact tracing”). This involves many factors in addition to the disinformation artifact itself. It’s the job of national security folks, not journalists or even subject matter experts. In the recent case, it turns out that attribution was easy based on the digital distribution chain, and in this case, we’re told that Iran is to blame (although it also involved data servers in Estonia).
Disinformation is multi-layered
Back to this past week’s stunt to try to intimidate voters, once there was consensus that the eMail and video were disinformation, it seemed clear that a certain male-only neo-fascist organization was part of the spurious story; and there were questions about whether that organization’s website had been penetrated in a cyber operation. Wait! That’s just more inference from the disinformation artifact, and among the objectives of the disinformation actor, could be causing the audience to believe that it was a combination cyber-operation and disinformation effort. Again, you just cannot squeeze any information out the artifact itself, much as the impulse is to try.
If the artifact suggests a cyber-operation, the responsible starting point is: there is no evidence of such a cyber-operation.
These points are just part of the lessons learned from this particular news cycle of this particular disinformation operation. Disinformation is part of the “new normal” of U.S. elections, and despite the attractions of the disinformation content, it needs to be covered factually, the same as any other falsehood in the national political narrative.
And in a race to break stories, it is easy to be tripped-up in the analysis, which will flaw the reporting.
Part 2: Some Simple Facts about Overseas “Ballot Fraud”
This recent effort discussed above in Part 1 by some group (possibly connected with the Proud Boys or vice-versa) sought to stoke fears about absentee ballot fraud, specifically large numbers of “overseas ballots” if we watch the video closely. Those fears could thrive in the absence of straight facts, so let’s set the record straight.
First, what are overseas ballots?
Specifically, a “Federal Write-In Absentee Ballot” (FWAB) often referred to as an “emergency backup ballot.” They’re used by a small specifically qualified class of military and overseas voters (called UOCAVA voters after the act that defined this class and services like FWABs for them), for a situation in which the voter is concerned that they might not receive their regular absentee ballot in time to return it in time to be counted. In those situations, the voter can make a “home made absentee ballot” and send it to their home county’s elections office.
Second, how does it work?
It’s not mysterious or difficult. There is a government program specifically for helping military voters, and anyone can go to their web site to download a PDF that explains it all. Go ahead, try it now if you like:
https://www.fvap.gov/uploads/FVAP/Forms/fwab.pdf
You’ll see that there is a page where the voter identifies herself, similar to how many states identify voters with info and signature on the outside of a special absentee ballot envelope—although in this case the information and signature go on a separate sheet in a plain envelope. And you’ll see page where one can literally write in things like: “San Mateo County Measure RR: No” instead of filling in the “No” bubble on a pre-printed ballot. And you’ll see instructions for how to prepare and perform the mail-back procedure.
Now, to the fraud part
Sure, anybody can grab this form and use it, including fraudsters pretending to be legitimate voters. And yes, it is not hard to find info about registered voters, in order to try to impersonate them.
Look at the form: voter’s name and address are required, those are a matter of public record from voter files. SSN and date of birth are also on the form, so a fraudster would have to use the so-called “dark web” to buy that information about a voter that the fraudster is targeting.
Turns out, that’s pretty easy to do for a very large portion of voters, because of security breaches that have exposed millions of American’s personal identifying information.
So, yes, some work is required, but a well-funded adversary could do it for many voters. In some sense the most annoying part of the process is printing the filled out forms, making a by-hand/ink signature, putting the forms in envelopes, and mailing them. The fact that a hand/ink signature is required means that fully automated mail-house services cannot be used, and the scheme requires the hands of people who don’t mind committing a real felony (or multiple felonies).
Next, here the key question:
How effective would such activities be, for a fraudster wanting to hack an election outcome?
Answer: not effective at all.
Specific points are below, but as I discuss in a separate voter fraud risk assessment essay, the key issue is not whether a fraud scheme is possible, but rather whether it is feasible to operate, undetected, at a scale large enough to influence an election outcome. The answer for using FWABs: it is not feasible, and here’s why:
- FWABs only work for voters whose registration shows that they are “UOCAVA voters.” That means that the set of targets for a fraudster is a very small percentage of voters.
- In a targeted county, all the UOCAVA voters have regular absentee ballots mailed to them, and many do mail them back in time. The regular absentee ballot is counted, if eligible. So the fraudster is limited to the subset of UOCAVA voters that don’t participate in an election at all, or not on time.
- Signature matching. Even if the fraudster gets all the correct information about a voter onto the FWAB form, and it matches the voter record of a voter tagged as UOCAVA, and even if that voter didn’t vote at all … still, election officials perform a check of the signature on the FWAB form, comparing to signature(s) on file. If the signature doesn’t match, the ballot is not eligible to be counted, though in some states an election official can write, call, or eMail the voter to let them know they had a signature problem and can try again.
So, really the fraudster’s only payback for effort is a case where a faked FWAB form exactly corresponds to a real UOCAVA voter, and the local election staff performing signature matching happens to make a mistake, and fails to catch the mismatch of the fraudster’s signature to the voter’s signature on file.
The actual yield might be zero. And the targets are few; most jurisdictions have 50 or less registered UOCAVA voters, and many receive zero FWABs. In 2018, there were only 7,284 FWABs in the entire country, as reported to the Election Assistance Commission. So, FWABs are rare, and easy to give special treatment to, for example, extra scrutiny of signatures to prevent false positive or false negative matches. Certainly, if a county got a lot more FWABs than the normal handful (if any) such extra scrutiny would be expected.
There you have it. Though such fraud schemes are feasible for a well resourced adversary to attempt, the payoff is hard to predict and might even be zero. Now, if an adversary is anticipating, for example, a very close (say, 537-vote-margin) presidential election in Florida (which has the most UOCAVA voters, about 140,000), one or two fraudulent FWABs might get counted, but even then, that’s not creating an effect on the outcome. To sway a very close election like that, adversaries have many more effective and scalable tools to lower turnout that could effect dozens or hundreds of voters, not ones and twos.
And with that, I return you to regularly scheduled election chaos, but hopefully armed with some insight on the reality distortion field it can cast.



